Why was a bitcoin node running on the New York City Board of Elections network??
Potential Evidence of Election Meddling we found back in 2016. Not sure why the powers that be & the media were not interested then. Perhaps, we informed the wrong outlets. Let’s try this again.
Summary
On 11/7/2016 at approximately 4pm EST, Matthew Caldwell, now founder and CEO of Tophat Security Inc. conducted a test of his Second Look program. The purpose of the test was to look for potential compromises in the United States’ Election Systems. Mr. Caldwell researched the publicly available information describing the ownership of Internet addresses that relate to the election process, election boards, parties, and correlated alleged compromised hosts. The primary finding was that his ‘Second Look’ process detected potentially infected or compromise hosts which exist in the U.S. election systems. These election systems were not only likely compromised but evidence of Bitcoin operations were also found. Bitcoin operations have been associated with illegal activities from murder to malware and are frequently used to launder money for illicit purposes. It is highly suspicious and unusual that an Electoral Board would be running Bitcoin on multiple systems. This document describes what was discovered during that test.
Correlated Alert Message
After correlation in our ‘Second Look’ process we received the following alert message:
“We have received Internet intelligence associated with IP address(s) indicating a potential compromise or other detrimental Internet activity.
These indications may uncover vulnerabilities or threats that are increasing information risk to the organization.
ALERT DETAILS:
ALERT IP:208.69.7.17 INTELSOURCE_ID:560 CUSTOMER_ID:42074
ALERT IP:208.69.7.17 INTELSOURCE_ID:561 CUSTOMER_ID:42074
ALERT IP:208.69.7.17 INTELSOURCE_ID:562 CUSTOMER_ID:42074
ALERT IP:192.111.57.168 INTELSOURCE_ID:485 CUSTOMER_ID:42074
ALERT IP:192.111.57.166 INTELSOURCE_ID:485 CUSTOMER_ID:42074
ALERT IP:192.111.57.160 INTELSOURCE_ID:459 CUSTOMER_ID:42074
ALERT IP:192.111.57.160 INTELSOURCE_ID:481 CUSTOMER_ID:42074
ALERT IP:192.111.57.160 INTELSOURCE_ID:485 CUSTOMER_ID:42074
Analysis of 192.111.57.x Board of Elections in the City of New York
This set of IP addresses was the most disturbing: 192.111.57.x series of addresses belongs to the NYS Board of Elections in New York City.
ALERT IP:192.111.57.168 INTELSOURCE_ID:485 CUSTOMER_ID:42074
ALERT IP:192.111.57.166 INTELSOURCE_ID:485 CUSTOMER_ID:42074
ALERT IP:192.111.57.160 INTELSOURCE_ID:459 CUSTOMER_ID:42074
ALERT IP:192.111.57.160 INTELSOURCE_ID:481 CUSTOMER_ID:42074
ALERT IP:192.111.57.160 INTELSOURCE_ID:485 CUSTOMER_ID:42074
Host:192.111.57.160
The intelligence sources for these IP addresses indicate that system 192.111.57.160 (Intel Source: 459) was compromised by the JIGSAW Family of Malware. This malware is generally ransomware, however can include other malware programs not previously detectable. Ransomware needs to be able to process bitcoin payments and the 192.111.57.160 host is running a BITCOIN NODE with BLOCKCHAIN activity (Intel Source:481,485) in the last 30 days.
Additionally, this information was correlated with an external third party called SHODAN.IO which shows the Bitcoin client version and last block information.
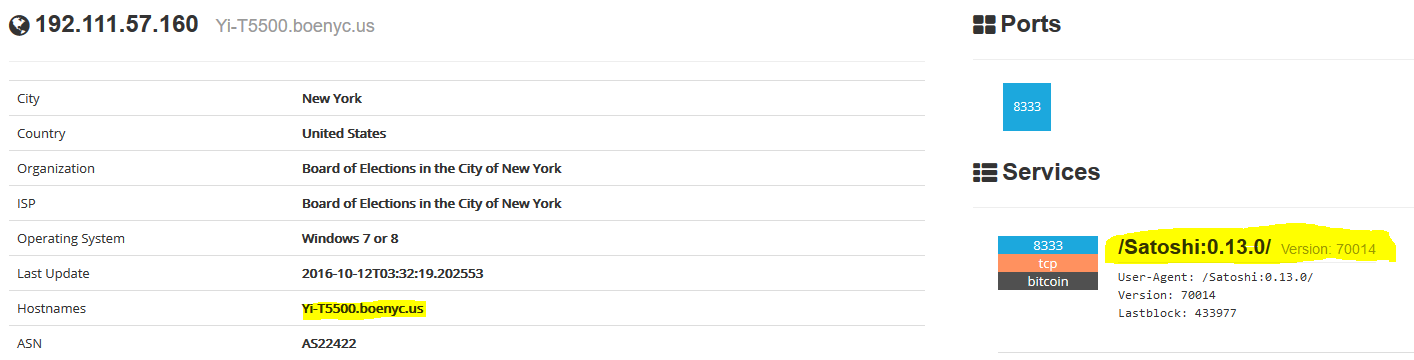
The first highlighted entry indicates the system is named Yi-T5500.boenyc.us. (Systems Administrator Yi Yu). This could be the administrator’s system running the bitcoin user agent on port 8333 tcp. This means that the system is being used to process bitcoin payments. Additionally, two other hosts are running bitcoin clients (On port 8333), the host 192.111.57.166 and 192.111.57.168 and have block chain information in the last 30 days.
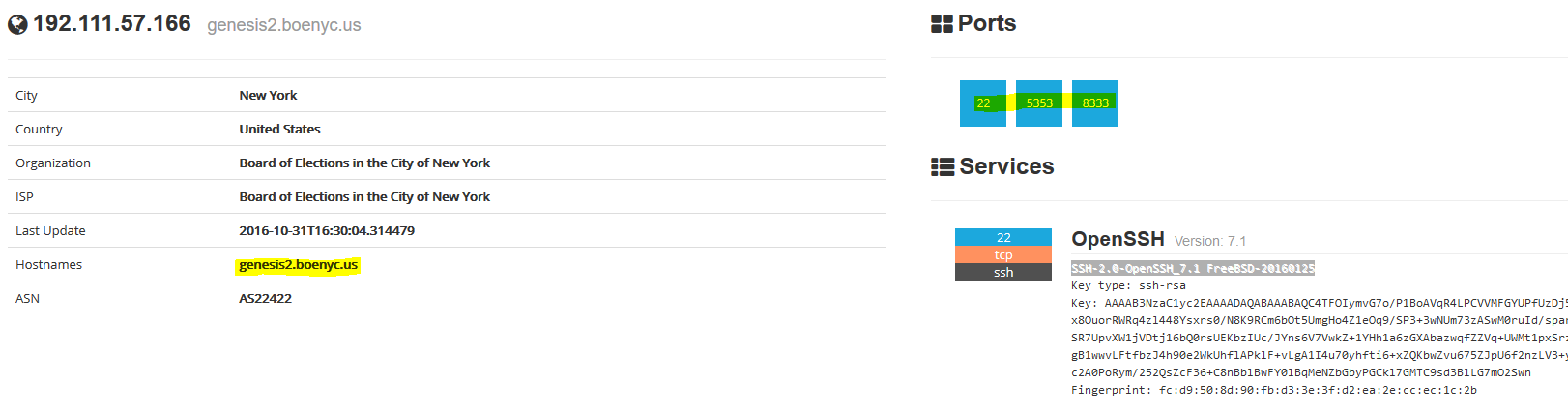
Host:192.111.57.166
This is from the host 192.111.57.166 and shows that the host is likely not a Windows system (likely FreeBSD) as it is running OpenSSH. This host is running a different version of the BITCOIN client (Satoshi:0.11.2) which is indicative that this bitcoin exchange client has been running on the server for a while and is unusual since normally ransomware doesn’t affect FreeBSD.
Host:192.111.57.168
Results for 192.111.57.168 could not be correlated in SHODAN.IO databases. However BITCOIN BLOCK Chain activity appears to have been present in the last 30 days.
The lP addresses 192.111.57.160-168 was reverse traced and found to belong to the following registrant, the entire network from these alerts belong to the organization.
NetRange: 192.111.56.0 – 192.111.63.255
CIDR: 192.111.56.0/21
NetName: BOARDOFELECTIONS-INTHECITYOFNEWYORK
NetHandle: NET-192-111-56-0-1
Parent: NET192 (NET-192-0-0-0-0)
NetType: Direct Assignment
OriginAS: AS22422
Organization: Board of Elections in the City of New York (BEICNY)
RegDate: 2013-01-29
Updated: 2015-07-16
Comment: http://vote.nyc.ny.us
Comment: Emergency Contact:
Comment: 347.827.1075
Ref: https://whois.arin.net/rest/net/NET-192-111-56-0-1
OrgName: Board of Elections in the City of New York
OrgId: BEICNY
Address: 42 Broadway, 6th Fl.
City: New York
StateProv: NY
PostalCode: 10004
Country: US
RegDate: 2012-09-18
Updated: 2012-09-19
Ref: https://whois.arin.net/rest/org/BEICNY
OrgAbuseHandle: YUYI-ARIN
OrgAbuseName: Yu, Yi
OrgAbusePhone: +1-212-487-7035
OrgAbuseEmail: yu@boenyc.us
OrgAbuseRef: https://whois.arin.net/rest/poc/YUYI-ARIN
OrgNOCHandle: YUYI-ARIN
OrgNOCName: Yu, Yi
OrgNOCPhone: +1-212-487-7035
OrgNOCEmail: yu@boenyc.us
OrgNOCRef: https://whois.arin.net/rest/poc/YUYI-ARIN
OrgTechHandle: YUYI-ARIN
OrgTechName: Yu, Yi
OrgTechPhone: +1-212-487-7035
OrgTechEmail: yu@boenyc.us
OrgTechRef: https://whois.arin.net/rest/poc/YUYI-ARIN
#
# ARIN WHOIS data and services are subject to the Terms of Use
# available at: https://www.arin.net/whois_tou.html
#
# If you see inaccuracies in the results, please report at
# https://www.arin.net/public/whoisinaccuracy/index.xhtml
#
Analysis of 208.69.7.17 Democratic National Mail Server
These are the alerts related to the DNC mail server:
ALERT IP:208.69.7.17 INTELSOURCE_ID:560 CUSTOMER_ID:42074
ALERT IP:208.69.7.17 INTELSOURCE_ID:561 CUSTOMER_ID:42074
ALERT IP:208.69.7.17 INTELSOURCE_ID:562 CUSTOMER_ID:42074
The following was of interest: 208.69.7.17 is the email server of the Democratic National Party (mailer.democrats.org) However, the Intelligence sources for this server indicate that it was on a SPAM blacklist. This is indicative of the server sending unsolicited emails to recipients on the Internet and seems to be a problem but not necessarily a compromise as one may surmise that this server send numerous emails.
The IP address 208.69.7.17 was reverse traced and found to belong to the following registrant, the entire network from these alerts belong to the organization.
NetRange: 208.69.4.0 – 208.69.7.255
CIDR: 208.69.4.0/22
NetName: DNC
NetHandle: NET-208-69-4-0-1
Parent: NET208 (NET-208-0-0-0-0)
NetType: Direct Assignment
OriginAS:
Organization: Democratic National Committee (DSCNC)
RegDate: 2006-07-24
Updated: 2012-03-02
Comment: http://www.democrats.org/
Ref: https://whois.arin.net/rest/net/NET-208-69-4-0-1
OrgName: Democratic National Committee
OrgId: DSCNC
Address: 430 South Capitol Street, S.E.
City: Washington
StateProv: DC
PostalCode: 20003
Country: US
RegDate: 2006-05-11
Updated: 2012-07-03
Ref: https://whois.arin.net/rest/org/DSCNC
OrgTechHandle: IIM3-ARIN
OrgTechName: Internet Infrastructure Manager
OrgTechPhone: +1-202-350-6012
OrgTechEmail: sysadmins@democrats.org
OrgTechRef: https://whois.arin.net/rest/poc/IIM3-ARIN
OrgAbuseHandle: IIM3-ARIN
OrgAbuseName: Internet Infrastructure Manager
OrgAbusePhone: +1-202-350-6012
OrgAbuseEmail: sysadmins@democrats.org
OrgAbuseRef: https://whois.arin.net/rest/poc/IIM3-ARIN
RTechHandle: IIM3-ARIN
RTechName: Internet Infrastructure Manager
RTechPhone: +1-202-350-6012
RTechEmail: sysadmins@democrats.org
RTechRef: https://whois.arin.net/rest/poc/IIM3-ARIN
#
# ARIN WHOIS data and services are subject to the Terms of Use
# available at: https://www.arin.net/whois_tou.html
#
# If you see inaccuracies in the results, please report at
# https://www.arin.net/public/whoisinaccuracy/index.xhtml
#

