Areas covered by Due DiligenceX
OT, ICS, SCADA, IOT, OEM equipment, Firmware, Software, Wireless, Radio Frequency and Hardware Analysis - All of these areas can be correlated by threats, vulnerabilities and zero-day exploits. Due Diligence X also correlates to the 50,000+ suppliers that manufacture connected equipment, including connected parts, through 7 levels of sub suppliers.
Current Industries DDX Security Supply Chain Equipment Supports
• Financial Services
• Oil and Gas Pipelines
• Health Care Institutions
• Multinationals
Why do you need a Supply Chain Cyber Risk Platform?
What areas of NIST-800-53-R5 and CMMC does DDX cover?
• NIST-800-53-R5
• SR-1 Policy and Procedures
• SR-2 Supply Chain Risk Management
• SR-3 Supply Chain Controls and Processes
• SR-4 Provenance
• SR-5 Acquisition Strategies, Tools and Methods
• SR-6 Supplier Assessments and Reviews
• SR-7 Supply Chain Operations Security
• SR-8 Notification Agreements
• SR-9 Tamper Resistance and Detection
• SR-10 Inspection of Systems or Components
• SR-11 Component Authenticity
• CMMC Level 4 and Level 5 Supply Chain Analysis, Threats and Risks
DDX Supply Chain Equipment Correlation Platform
Software Code - Decompile and Analysis
100’s of Microcode and Languages
Firmware Analysis Engine
Intel, AMD, ARM and MIPS + more
Hardware - AI/ML Analysis
Over 500,000 Unique Hardware Systems
RF - Analysis
VLF, HF, VHF, UHF, SHF Frequencies
Analog and Digital Modes
Vulnerability Management Analysis
Identified 4400 Vulnerabilities in third party vendors and 10 zero day exploits
Vendor Tracking Correlation
50,000 Manufacturers, Suppliers and Vendors Threat Tracking in Near Real-time
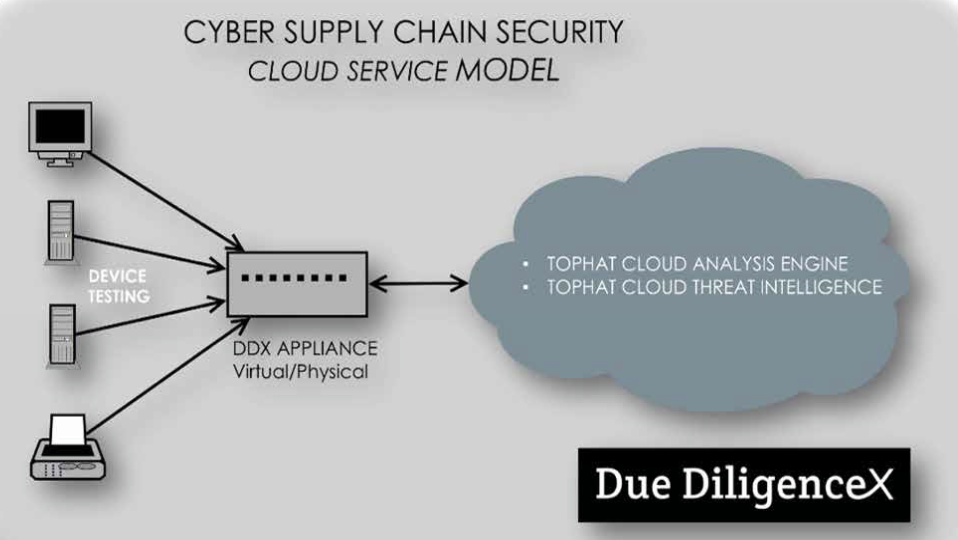
Clients can have it installed on a server, laptop, cloud (AWS/Azure), virtual appliance (VMWare/HyperV) or a purpose-built hardened appliance. This appliance can be completely disconnected from a corporate network or positioned in a remote area that only has cellular / mobile connectivity.
Why Secure the Cyber Supply Chain?
Purchasing equipment from vendors who receive their components from all over the world, including countries that may have malicious intent directed at the United States, has greatly increased the risk to the Supply Chain.
Global Threat Analysis
Due Diligence X© (DDX) was created with this in mind – to provide a dynamic platform for testing devices for assurance that the equipment will be free from a variety of security threats. The DDX model recognizes that infrastructure components of the Supply Chain have significant relationships to global industries.
As a result, DDX incorporates into its Supply Chain testing the geo-location and vendor data from its Cloud based Threat Intelligence Engine in order to provide a more comprehensive view of the resident component risks.
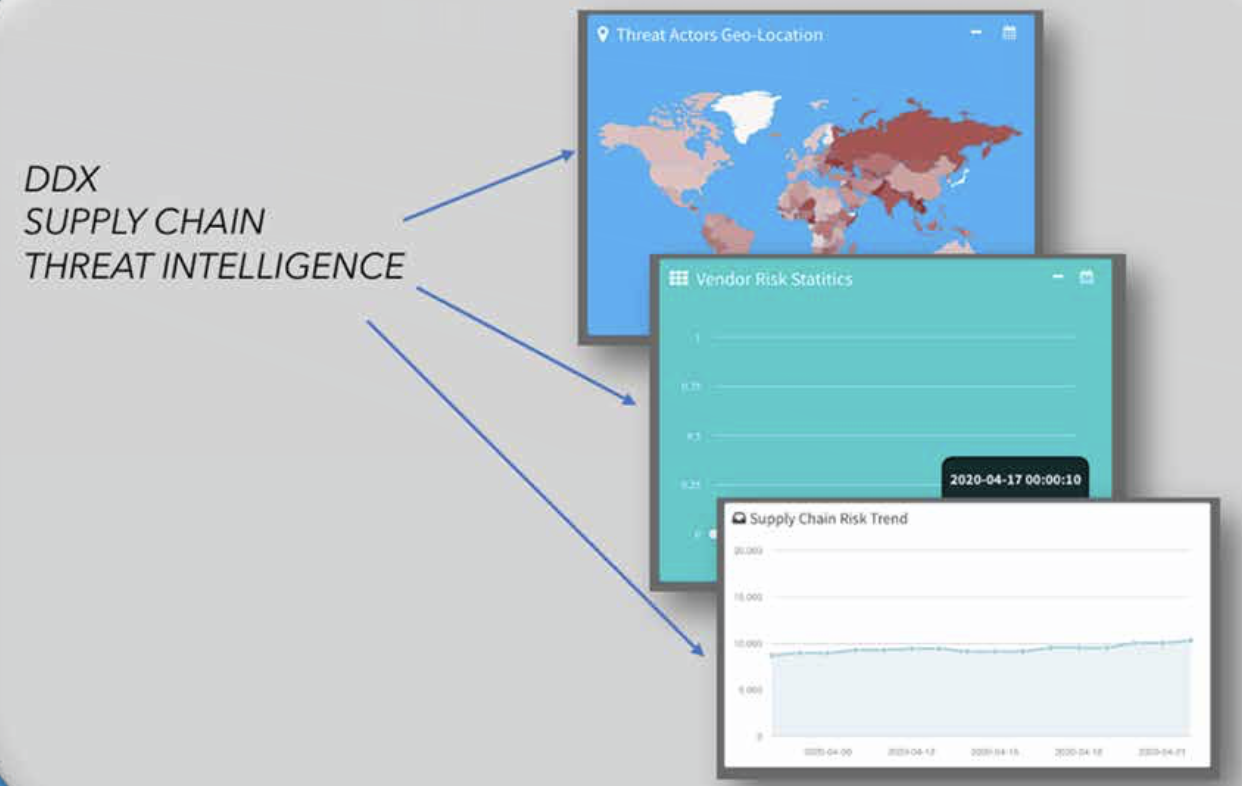
Situational Awareness and Potential Threats
Geo-Location
Threats based on the country of origin
Vendor Risk
Data compiled for a wide-range of suppliers
Risk Trends
Indicators of the trends for the Supply Chain
Geo-Location
Threats based on the country of origin
Vendor Risk
Data compiled for a wide-range of suppliers
Risk Trends
Indicators of the trends for the Supply Chain
Device Testing
Management and Control
Methodology
Architecture
- Onsite quarantine for devices
- Local appliance virtual/physical
- Cloud threat/analysis intel
Admin Control
- Profiles: Testing set up for the quarantine duration and the type of tests to be performed
- Schedules: Initiating testing and controlling the frequency and duration of the testing for the devices
- Status: Real-time view of the testing status and alerts online regarding security threats
DDX Features
Reports: The Results from DDX are provided in a variety of detail, using a number of delivery mechanisms to equip the security personnel with the tools for risk mitigation and response:
Summary Reports: High level view of the results from the testing of the devices for management review and analysis
Detail Reports: Specific information from the testing that enables administrators to identify the threat levels and granular data for mitigation
Alerts: Notification from the testing that is provided for significant risks that are detected
Dashboard: Composite of the risk levels from the testing, with aggregated data for geo-location, vendor, and Supply Chain threat
